Saviynt Blog
Stay up to date on the latest security news, research and more.
Content Hub
Industry
Solutions





12 / 20 / 2023
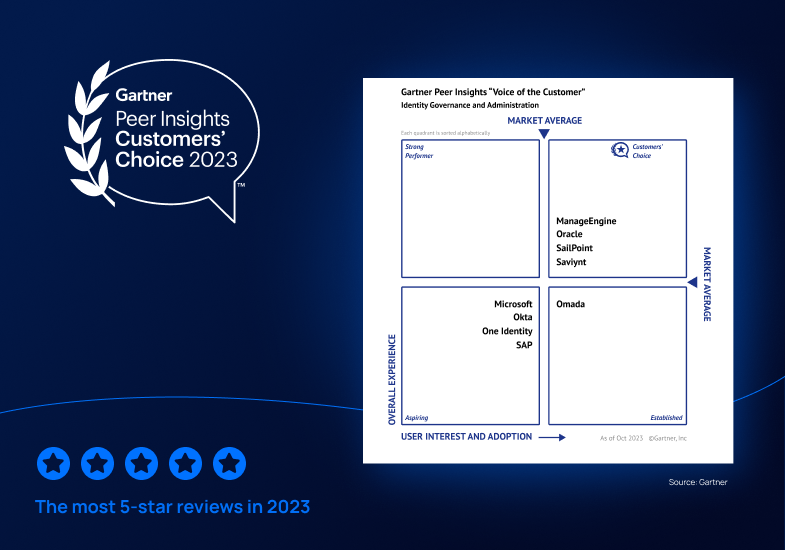
Saviynt a Gartner® Peer Insights™ Customers' Choice in Identity Governance and Administration—Three Years in a Row
READ BLOG




























04 / 17 / 2023
Choosing a Cloud Privileged Access Management (PAM) Solution?: Three Must-Ask Questions
READ BLOG













01 / 05 / 2023
Saviynt Recognized as a 2022 Gartner® Peer Insights™ Customers’ Choice in Identity Governance and Administration
READ BLOG




12 / 13 / 2022
Saviynt EIC Scores 95/100 for Core Criteria in the 2022 Gartner® Solution Comparison for Identity Governance and Administration¹
READ BLOG









08 / 17 / 2022
3 Key IGA Modernization Must-Haves: All the Features, None of the Compromise
READ BLOG






07 / 06 / 2022
Top Challenges to Achieving Enterprise-Wide Visibility of Privileged Access
READ BLOG